Laptop: <a href="http://www.shutterstock.com/pic-170119073/stock-photo-customer-chatting-to-a-call-centre-online-with-an-image-of-the-female-operator-on-the-screen-of-his.html?src=_IVnFChhIxXIDyhV0t2npA-1-122">Gajus</a>/Shutterstock; Window: <a href="http://www.shutterstock.com/pic-115727878/stock-photo-colorful-computer-window-isolated-on-white-background.html?src=MquiqlLWm9nPOZ_3uAc4JA-1-0">Tashatuvango</a>/Shutterstock; Woman: <a href="http://www.shutterstock.com/pic-166796783/stock-photo-hiding.html?src=UfwzKB7bNe1VN-WXkNDpTQ-1-36">Nomad_Soul</a>/Shutterstock; Blackshades screen: <a href="www.symantec.com/connect/blogs/blackshades-coordinated-takedown-leads-multiple-arrests">Symantec</a>
On Monday, US officials announced the arrest of more than 90 people allegedly connected to an organization called Blackshades, which sold software that allows hackers to easily take over a Microsoft Windows computer remotely. Last year, a college student used the tool to take nude photos of Miss Teen USA via her personal computer’s webcam. According to the FBI and law enforcement officials, the program has been sold and distributed to “thousands” of people in more than 100 countries since 2010, affecting some 700,000 victims. Here’s why you might want to update your anti-virus software, or, if you’re prone to dancing around your room naked, at least put a piece of tape over your webcam.
What is Blackshades?
Blackshades is the name of an organization allegedly owned by a Swedish 24-year-old named Alex Yücel. According to government officials, Yücel and Michael Hogue?, a 23-year-old US citizen who was arrested in 2012 as part of the feds’ tangential investigation into Blackshades, codeveloped the Blackshades remote access tool (RAT). This tool, which sold for as little as $40 at bshades.eu and other sites, essentially allowed buyers to act as peeping Toms on strangers’ computers. The organization made more than $350,000 between September 2010 and April 2014, according to the FBI.
How does the Blackshades Remote Access Tool (RAT) work?
The Blackshades RAT isn’t any different than what your IT person at work uses to get remote access to your computer, explains Runa Sandvik, staff technologist at the Center for Democracy & Technology (CDT). But if your IT department were accessing your computer, “you’d have a heads up,” she says. “In this case you won’t even know [the hacker] is on your computer.”
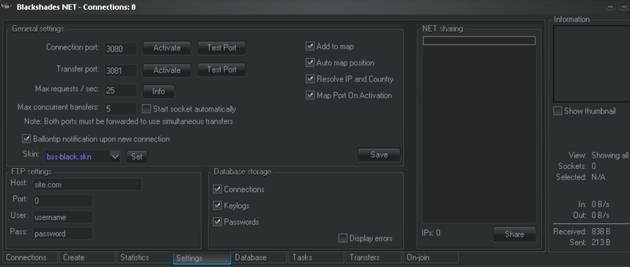
After buying a copy of the RAT software, a hacker has to install the program on a target’s computer, by, say, deceiving a person into clicking on a malicious link. Then, once the hacker has access to a computer, he or she can then use the RAT software to easily record a person’s keystrokes or passwords, take screenshots, rummage through computer files, or turn on the person’s web camera, according to the feds. Anything you can do on your computer, the hacker can do, too. And the software makes it all super easy. In fact, it’s “marketed principally for buyers who wouldn’t know how to hack their way out of a paper bag,” writes Krebson Security. Here’s what the command and control panel looks like:
The program also includes “spreaders,” which help hackers send out malicious links from peoples’ social-media accounts, and a file hijacker tool. That tool, according to the FBI press release, allows users “to encrypt, or lock, a victim’s files and demand a ‘ransom’ payment to unlock them. The RAT even came with a prepared script demanding such a ransom.”
What do hackers use remote access tools for?
The FBI says the Blackshades RAT has been used to exploit credit cards, bank accounts, and personal information. But perhaps the creepiest way people can use remote accessing tools is to take photos and video via webcam. In November of last year, a college student pleaded guilty to hacking the webcam of Miss Teen USA Cassidy Wolf with the Blackshades software, and attempting to blackmail her. He allegedly said he had up to 40 other “slave computers,” according to the original criminal complaint.
Last year, Ars Technica wrote about a thread on a hacker forum that was more than 134 pages long and filled with images captured through unsuspecting women’s webcams. Hackers wielding remote accessing tools—it’s unknown whether they were using Blackshades or other software—called the women their “slaves” and wrote about picking out “the ‘good’ [sexual] stuff” and categorizing it using names and passwords, according to the news outlet. And last year, a 17-year-old boy in Detroit paid hackers in the Philippines more than $1,000 in blackmail money after they collected video of him via webcam. This tool has been used for political purposes as well. In 2012, the software was sent by alleged pro-government attackers to try and infect the computers of anti-government Syrian activists.
Now that people have been arrested in connection with Blackshades, does this mean I’m in the clear?
Nope. While the sale of Blackshades software, whose main website has now been shut down, was already on the decline (there were more than 1,300 infections last spring, but fewer than 400 in April 2014, according to Symantec), there are other remote accessing tools out there. “Even if there are just 100 people using Blackshades, there are another 100 using a tool with a different name that works exactly the same way,” says CDT’s Sandvik. Additionally, it’s not clear that the FBI will be able to get the Blackshades charges to stick. As the Daily Beast notes, it may be hard for prosecutors to prove whether the defendants who possessed the software used it for illegal activity.
What should I do to keep my computer private?
Follow best security practices. The FBI and security experts recommend that you update your software, including anti-virus software, install a good firewall, don’t open suspicious email attachments or URLs—even if they come from people on your contact list—and create strong passwords. The FBI has also published a list of files that you can search for on your hard drive to see if your computer has been infected. “Regardless of the specific kind, if you get malware on your system, it’s bad,” says Christopher Budd, a spokesman for Trend Micro, a Japanese security software company. “But people shouldn’t worry about malware, they should take concrete steps.” And if you put tape over your webcam, too, no one will judge you. “I do,” says Sandvik.